Introduction
In today’s digital landscape, protecting sensitive data and ensuring system security is more important than ever. Cyber threats and breaches continue to evolve, challenging businesses and individuals to adopt effective and resilient security measures. The core elements of information security—Confidentiality, Integrity, and Availability (CIA)—serve as a framework for developing robust security strategies. By understanding these principles, implementing defense-in-depth tactics, and leveraging various security controls, you can better safeguard critical assets against unauthorized access, tampering, and disruption.
The CIA Triad: The Pillars of Information Security
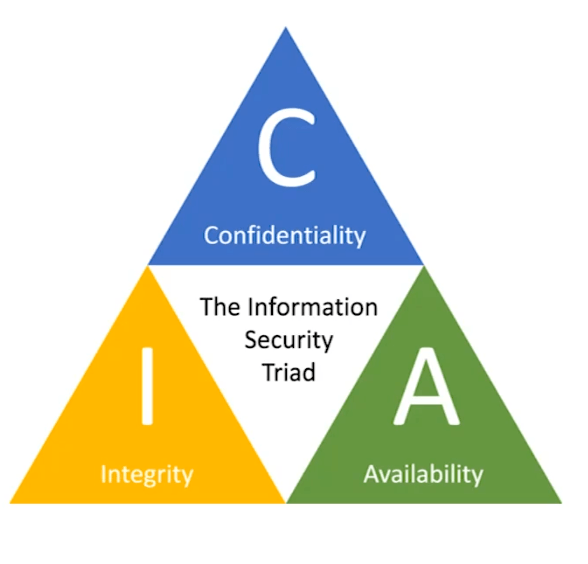
The CIA triad is a foundational model for designing and evaluating security systems. It emphasizes three key principles: Confidentiality, Integrity, and Availability. Together, they provide a comprehensive approach to data and system protection.
- Confidentiality: Confidentiality ensures that sensitive data is accessible only to authorized individuals and entities. Unauthorized access, whether by malicious actors or accidental exposure, poses a significant risk to organizations and individuals. To maintain confidentiality, organizations often use encryption, strong access controls, and authentication mechanisms. Consider online banking, where sensitive financial data is protected by multi-factor authentication (MFA), ensuring only verified users can access their accounts. Breaches of confidentiality can lead to reputational damage, legal consequences, and loss of trust.
- Integrity: Data integrity ensures that information remains accurate and unaltered, except by authorized modifications. This principle protects against unauthorized changes, deletions, and tampering, maintaining the reliability and accuracy of critical data. Integrity is particularly crucial for financial records, healthcare data, and legal documents. Techniques like checksums, hash functions, and digital signatures help verify data integrity. For example, a tamper-evident seal on a document or a cryptographic hash of a file ensures that unauthorized alterations are detectable.
- Availability: Availability ensures that data and systems are accessible to authorized users when needed. Downtime, system failures, or malicious attacks, such as Denial-of-Service (DoS) attacks, can disrupt availability, impacting productivity and customer satisfaction. High availability systems, redundancy, regular backups, and disaster recovery plans all contribute to maintaining availability. For instance, cloud-based services often have multiple data centers and failover systems to ensure continuous availability even during outages.
The CIA triad serves as a balancing act. Increasing confidentiality may reduce system usability, while improving availability might introduce security risks. Therefore, an effective security strategy finds a balance among these three elements, aligning with the organization’s needs and risk tolerance.
Defense-in-Depth: Layered Security Strategy
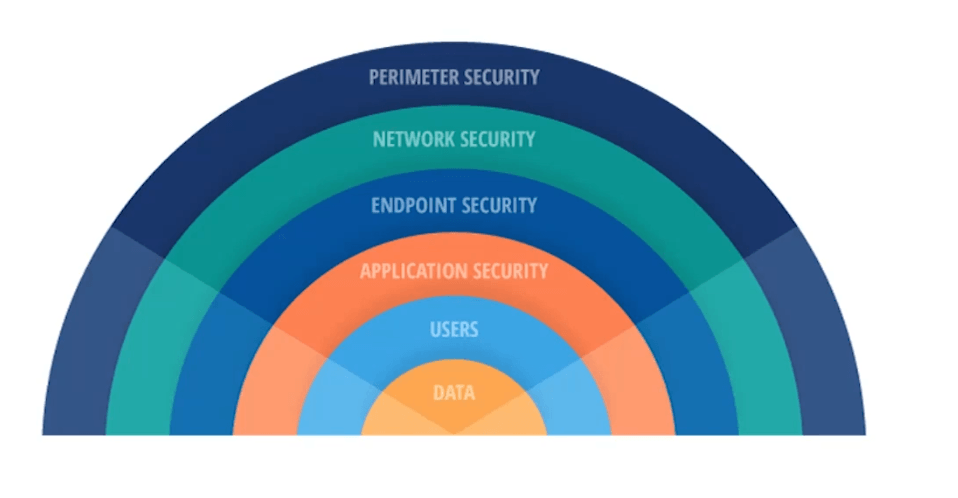
Defense-in-depth is a security approach that uses multiple layers of protection to mitigate risks and minimize potential attack success. This concept assumes that no single security measure is foolproof, so multiple defenses must work together to safeguard assets. Here’s how it works at different levels:
- Perimeter Security: This outer layer defends against threats originating from outside the organization’s network. Firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) monitor and block unauthorized access attempts.
- Network Security: Once inside the network, additional measures such as network segmentation, access control lists (ACLs), and internal firewalls provide further protection. By isolating critical systems and data, organizations limit the potential impact of breaches.
- Endpoint Security: Individual devices, such as computers, smartphones, and tablets, are protected through antivirus software, patch management, and endpoint detection and response (EDR) tools. These measures help prevent malware infections and unauthorized access at the device level.
- Application Security: Applications often serve as entry points for attackers, making it essential to secure them through vulnerability assessments, code reviews, secure coding practices, and input validation.
- Data Security: Sensitive data is protected through encryption, data masking, access controls, and secure storage practices. Encrypting data in transit and at rest ensures that unauthorized individuals cannot access its contents.
- User Security: Users are often the weakest link in security. Training employees on security best practices, enforcing strong password policies, and using multi-factor authentication (MFA) helps reduce human-related risks.
The goal of defense-in-depth is to create multiple layers of defense that an attacker must penetrate, increasing the complexity and cost of a successful breach. For example, if a cybercriminal bypasses the network firewall, they may still encounter robust endpoint security measures and data encryption, preventing them from accessing sensitive information.
Active Defense Strategies in Cybersecurity
Beyond passive defenses, organizations can adopt active defense strategies to detect, mitigate, and counteract cyber threats. These strategies include:
- Annoyance: This approach involves wasting an attacker’s time and resources, often through the use of honeypots or decoy systems. Honeypots mimic valuable targets but are isolated from the real network, allowing security teams to monitor and learn from attackers’ behaviors without endangering sensitive data. By leading attackers astray, organizations can gain valuable insights and develop countermeasures.
- Attribution: Identifying the source of an attack, whether it be an individual, organization, or nation-state, can be crucial for law enforcement and mitigation efforts. Techniques for attribution include tracking IP addresses, analyzing malware signatures, and monitoring attack patterns. While attribution can be challenging due to obfuscation techniques used by attackers, it can provide valuable intelligence for response strategies.
- Attack (Hacking Back): In some cases, organizations may choose to retaliate against attackers by targeting their systems or disrupting their operations. However, this approach is legally and ethically contentious and often discouraged. The risks of escalation, collateral damage, and legal ramifications make hacking back a last resort that should be approached with extreme caution.
Critical Terminology in Information Security
A solid understanding of key terminology is essential for effective communication and strategic planning in information security:
- Hack Value: The perceived worth of a target to an attacker, often dictating their motivation to pursue a breach. High-profile targets, such as financial institutions or government agencies, often have high hack value.
- Vulnerability: A weakness or flaw in a system, process, or application that can be exploited by attackers to compromise security.
- Exploit: A specific method or tool used to take advantage of a vulnerability.
- Payload: The component of an exploit that performs the malicious action, such as stealing data or deploying ransomware.
- Zero-Day Attack: An attack that exploits a previously unknown vulnerability, for which no patch or defense exists at the time of discovery. Zero-day attacks are particularly dangerous due to their novelty and lack of countermeasures.
Security Controls and Their Functions
Security controls are measures implemented to reduce risk and protect assets. They are categorized into three main types:
- Physical Controls: These tangible measures prevent unauthorized access to physical assets. Examples include locks, security guards, surveillance cameras, fences, and bollards. Physical controls deter intruders, provide evidence, and restrict access to sensitive areas.
- Administrative Controls: Policies, procedures, and guidelines set by management to minimize risk. Examples include security policies, employee training, incident response plans, and best practice enforcement. Administrative controls establish a framework for behavior and help ensure compliance with security standards.
- Technical Controls: Technology-based mechanisms that enforce security measures. Examples include firewalls, intrusion detection systems (IDS), antivirus software, encryption, and access controls. Technical controls are often the first line of defense against cyber threats.
Security controls can also be classified based on their function in the security lifecycle:
- Preventive Controls: These measures aim to stop threats before they occur, such as firewalls, access controls, and encryption.
- Detective Controls: These measures identify and report incidents as they happen, including intrusion detection systems, audits, and monitoring.
- Deterrent Controls: Designed to discourage attackers, such as warning signs, security lighting, and surveillance cameras.
- Mitigating or Recovery Controls: Minimize the impact of an incident by isolating systems, containing damage, and restoring operations quickly.
Network Security Zoning and Access Control Models
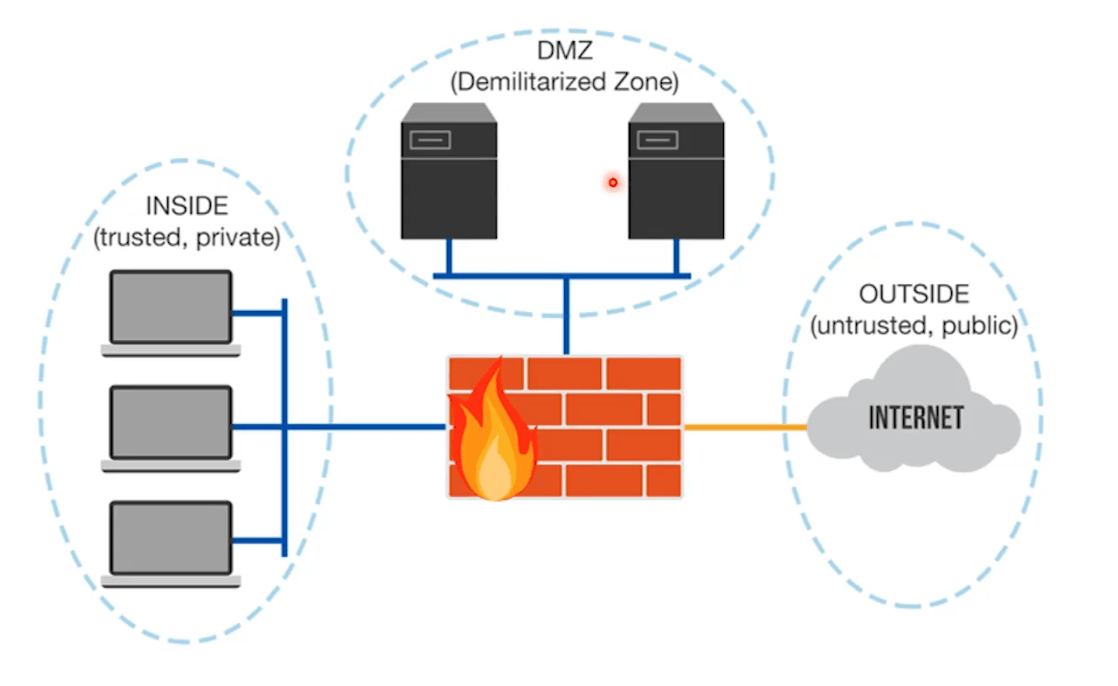
Network security zoning involves segmenting a network into different zones based on security needs and access requirements. By creating distinct zones, organizations can control access and minimize risk. Common zones include:
- Internet Zone: The public-facing portion of the network that interacts with external users and systems.
- DMZ (Demilitarized Zone): A controlled zone that acts as a buffer between the public internet and the internal network. It often hosts public-facing servers, such as web servers.
- Intranet Zone: The internal network for employees and trusted systems, typically subject to stricter security controls.
Access control models define how permissions are granted and managed:
- Mandatory Access Control (MAC): Typically used in government and military settings, MAC assigns security labels and clearances to users and data, strictly controlling access based on sensitivity levels.
- Discretionary Access Control (DAC): Resource owners determine who can access their data or systems, providing flexibility but potentially increasing risk.
- Role-Based Access Control (RBAC): Permissions are assigned based on users’ roles or job functions, reducing administrative complexity and enhancing scalability.
- Rule-Based Access Control: Access is granted or denied based on rules and conditions, often used in firewalls and network devices.
Practical Applications and Real-World Scenarios
Consider the following practical examples of security measures and access control in action:
- Encryption: Online shopping platforms use HTTPS to encrypt data exchanged between customers and websites, ensuring that sensitive payment information remains secure.
- Access Control Lists (ACLs): Network administrators use ACLs to specify which users or systems can access specific resources or network segments.
- Audit Logs: Organizations maintain audit logs to trace user activities, ensuring accountability and compliance with security policies.
Conclusion
Information security is an evolving field that requires constant vigilance and a multi-layered approach to defense. By understanding and implementing the elements of the CIA triad, employing defense-in-depth strategies, and utilizing various security controls, individuals and organizations can protect their data and systems against a wide range of threats. Staying informed, proactive, and adaptable is key to building a resilient security posture in the face of ever-changing cyber risks.
![habitable_solution logo 2024 [t-w]](https://habitablesolution.com/wp-content/uploads/2025/02/habitable_solution-logo-2024-t-w.png)



