(What the Experts—and Hackers—Wish You Knew in 2024)
Introduction: Why You Should Care About “Best Practices”
Let’s get real—most people know their passwords aren’t perfect, but few realize just how much the rules of the game have changed. Forget what you learned a decade ago about swapping out your password every 30 days or using “Tr0ub4dor&3” as the gold standard. Cybersecurity evolves constantly, and so do the tricks hackers use.
If you want to protect your accounts—and your peace of mind—it’s time to get up to speed with the latest, battle-tested advice used by top organizations, tech giants, and digital security pros. In this post, you’ll learn the newest industry best practices for passwords, why they matter, and what you can do today to keep your digital life locked tight.
The Evolution of Password Policy: From Complexity Theater to Real Security
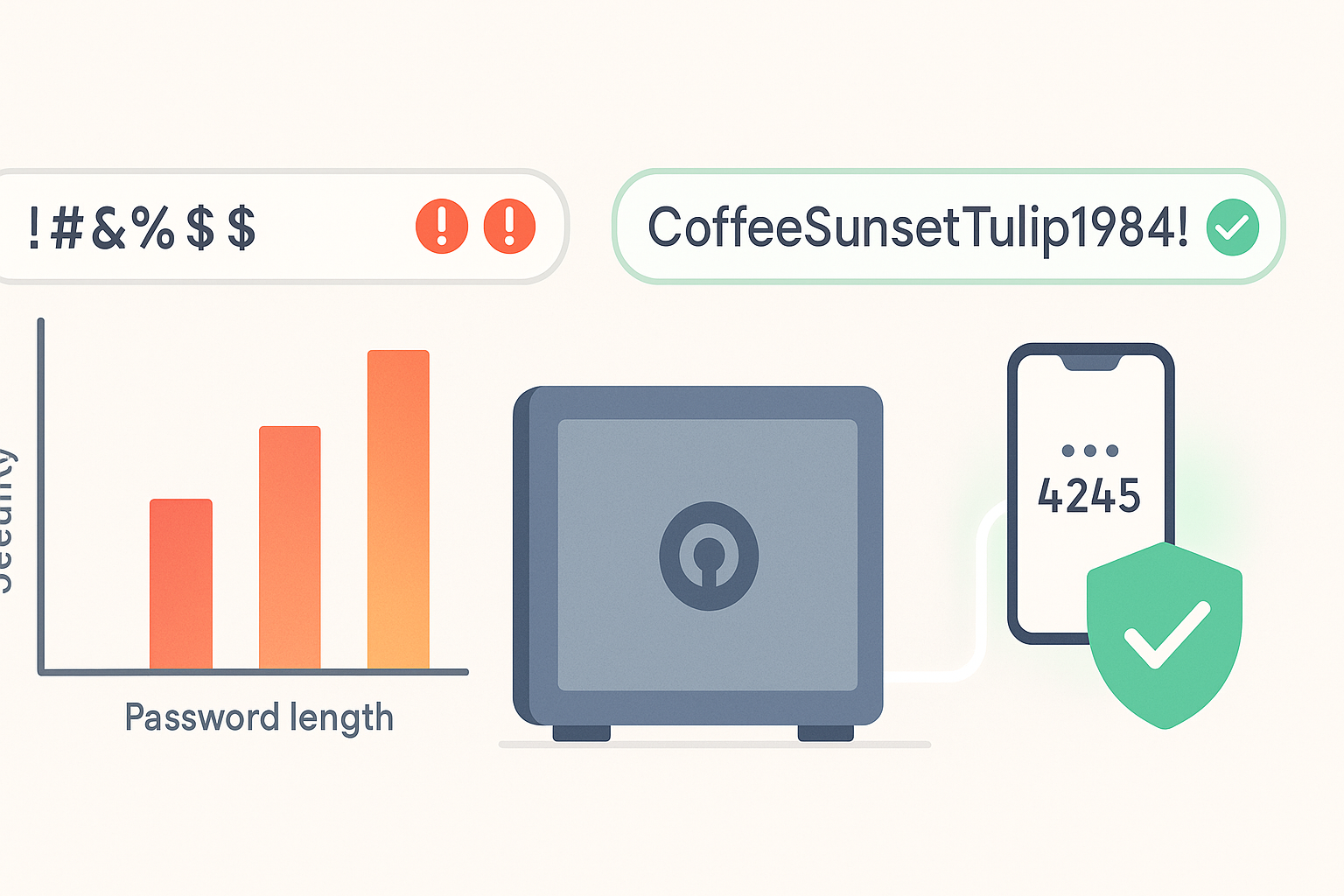
Remember when sites forced you to change your password every 30 or 90 days, demanded a capital letter, number, symbol, and DNA sample… then made you answer, “What’s your first pet’s favorite band?”
We now know those rules caused more harm than good:
- People picked weaker passwords just to remember them.
- Many would write them on sticky notes or reuse “base” passwords with a small tweak (“Password1!” becomes “Password2!”).
- Hackers caught on—and got faster.
Modern password policy is about making security usable and effective for real humans. Here’s how:
Best Practice #1: Length Beats Complexity (Every Time)
Industry guidance has shifted. The U.S. National Institute of Standards and Technology (NIST)—the gold standard for password recommendations—now emphasizes length over mandatory complexity.
- Aim for passwords of 12 characters or more.
- Passphrases (multiple, unrelated words) are highly recommended.
- Don’t force weird complexity rules if they make passwords hard to remember.
Why?
A longer password is exponentially harder to brute-force. “myfavoritebluecoffee” is stronger than “B!7z4” and far easier to recall.
Best Practice #2: Unique Password for Every Account
Still reusing the same password for social, email, and banking? You’re playing with fire.
Credential stuffing is rampant: hackers use stolen passwords from one site to break into others. Even if a shopping site gets hacked, your email or bank could be next.
The rule:
Every single account—especially sensitive ones—must have its own unique password.
Best Practice #3: Use a Password Manager—No Excuses
No one expects you to remember 50+ unique, strong passwords.
That’s where password managers shine.
These digital vaults generate, store, and auto-fill passwords for you, so you only have to remember one master password.
Top picks:
- 1Password
- Bitwarden
- Dashlane
- LastPass
Most browsers (Chrome, Firefox, Safari, Edge) also offer built-in managers, but third-party options are generally more secure and feature-rich.
Best Practice #4: Avoid Outdated “Security Theater”
- No more forced periodic password changes:
Unless you suspect a breach, you don’t need to change your passwords regularly.
Frequent forced changes lead to bad habits and weaker passwords. - Ban password hints:
They often give attackers extra clues. Security questions can be guessed or found on social media (“mother’s maiden name,” “first car,” “favorite color”). - Don’t allow context-specific passwords:
Never use your username, email, or site name in your password.
Best Practice #5: Ban Common Passwords
Modern systems should block the most common passwords automatically:
- “123456”
- “password”
- “qwerty”
- “iloveyou”
- And similar patterns
If you’re running a site, enforce this. If you’re a user, avoid these at all costs.
Best Practice #6: Enable Multi-Factor Authentication (MFA) Everywhere
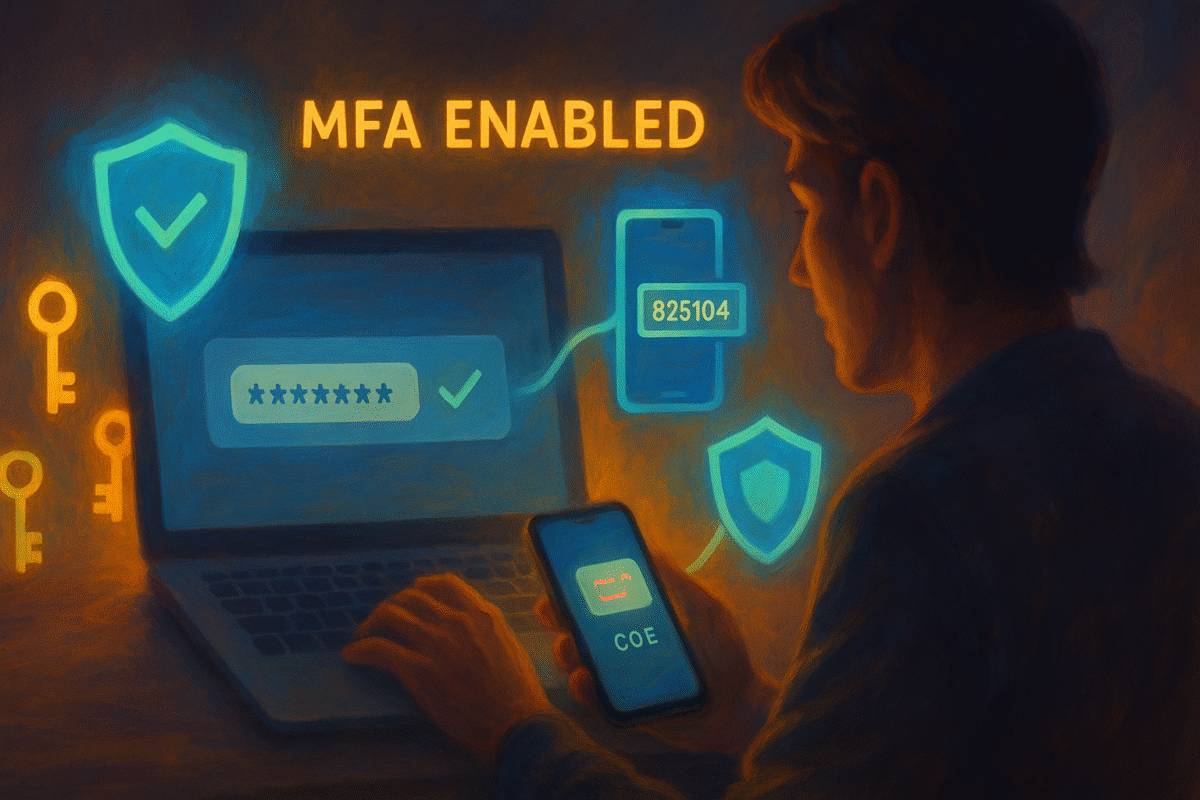
No matter how strong your password, one breach or phishing scam can ruin everything.
Multi-Factor Authentication (MFA) requires something you know (your password) and something you have (a phone, an app code, a hardware key, biometrics).
- Use an authenticator app (Google Authenticator, Authy, Microsoft Authenticator)
- SMS is better than nothing, but can be intercepted—use app-based codes or hardware keys for important accounts
Best Practice #7: Educate Yourself About Phishing and Social Engineering
Even the best password can be stolen if you’re tricked into handing it over.
- Never enter your password after clicking a suspicious link.
- Always check the URL before logging in.
- Treat unsolicited “security alerts” with skepticism.
Remember:
Security is a mindset. Stay curious, alert, and never be afraid to verify.
Bonus: Monitor for Breaches
- Check if your accounts appear on Have I Been Pwned.
- Many password managers will alert you to reused or breached passwords.
- Update your passwords immediately if you learn of a compromise.
Quick Reference: 2024 Password Policy Checklist
- At least 12 characters—preferably more
- Passphrases over complex gibberish
- Unique password for every account
- Use a password manager
- Enable MFA everywhere
- Avoid common passwords and context-specific info
- No forced periodic changes (unless breached)
- Educate yourself on phishing and scams
- Regularly check for breaches
- Ban password hints and weak security questions
Conclusion: Make Your Passwords (and Habits) Bulletproof
The world of password security has changed. Old-school rules are out; smart, user-friendly best practices are in.
By following these industry-backed guidelines, you’re not just following the crowd—you’re outsmarting the hackers and protecting what matters most.
Take action today:
Audit your passwords. Install a manager. Turn on MFA.
Share this post with friends, family, and colleagues—they’ll thank you when their digital lives stay safe.
Next up: We’ll dive into the latest defenses—rate limiting, lockouts, and the real magic of multi-factor authentication.




