Picture this: You wake up, roll over, and check your phone. There’s a notification from your favorite app. You grab your coffee, scroll through email, maybe log into a few accounts—banking, social media, shopping, streaming.
But have you ever stopped to wonder just how many digital doors you’re unlocking every day? And more importantly—how secure are those doors, really?
If you’re like most people, you have dozens, maybe even hundreds, of online accounts. Each one is a potential entry point for cybercriminals. In a world where our lives are increasingly lived online, cybersecurity is no longer just for IT pros or secret agents.
It’s for everyone—including you.
Today, we’re starting a series to help you not just survive the digital jungle—but thrive in it, confidently and securely. This isn’t your average “change your password” lecture—this is your inside look at how hackers think, what defenses actually work, and how you can take practical steps (starting today!) to keep your digital life safe.
Security in the Physical World: The Doorway Metaphor

Let’s start simple: security is something we all understand in the real world.
You wouldn’t leave your front door wide open at night, right?
You might lock your car, set up a security camera, maybe even install a home alarm.
Why?
Because you know that while most people are honest, some aren’t. That little lock on your door isn’t a guarantee against every intruder—but it’s a strong deterrent, a way of saying: “This space is protected.”
In cybersecurity, the principle is the same.
But instead of keys and locks, we have usernames, passwords, and authentication codes.
The trick is: our “doors” are now invisible, and the thieves are silent, persistent, and sometimes halfway across the world.
Digital Doors: What Are We Protecting?
Your digital life is made up of accounts—dozens of them. Email, social media, banking, work, streaming services, online shopping, cloud storage, dating apps, gaming platforms, the list goes on.
Each account is like a room in a giant virtual house.
If an attacker gets the “key” (your password), they don’t just get into the room—they might gain access to your entire house.
But here’s the problem:
Most people use the same key for every room.
If a thief finds one key under your doormat, they can unlock every door you own.
Sounds terrifying?
It should. But don’t panic—knowledge is the best defense.
Authentication and Authorization: Who Are You, and What Can You Access?
Cybersecurity starts with two core concepts:
- Authentication: Proving you are who you say you are.
- Authorization: Deciding what you’re allowed to do once inside.
Let’s bring it back to our house analogy:
- Authentication is showing your ID to the doorman.
- Authorization is whether the doorman lets you into the lobby or the penthouse.
Most websites use usernames as a public identifier—everyone knows your name. But your password is your secret—your key.
When you type both, you’re proving you’re the real owner of that key.
But here’s the catch:
If someone else gets your password, they can pretend to be you.
That’s why password security matters more than you think.
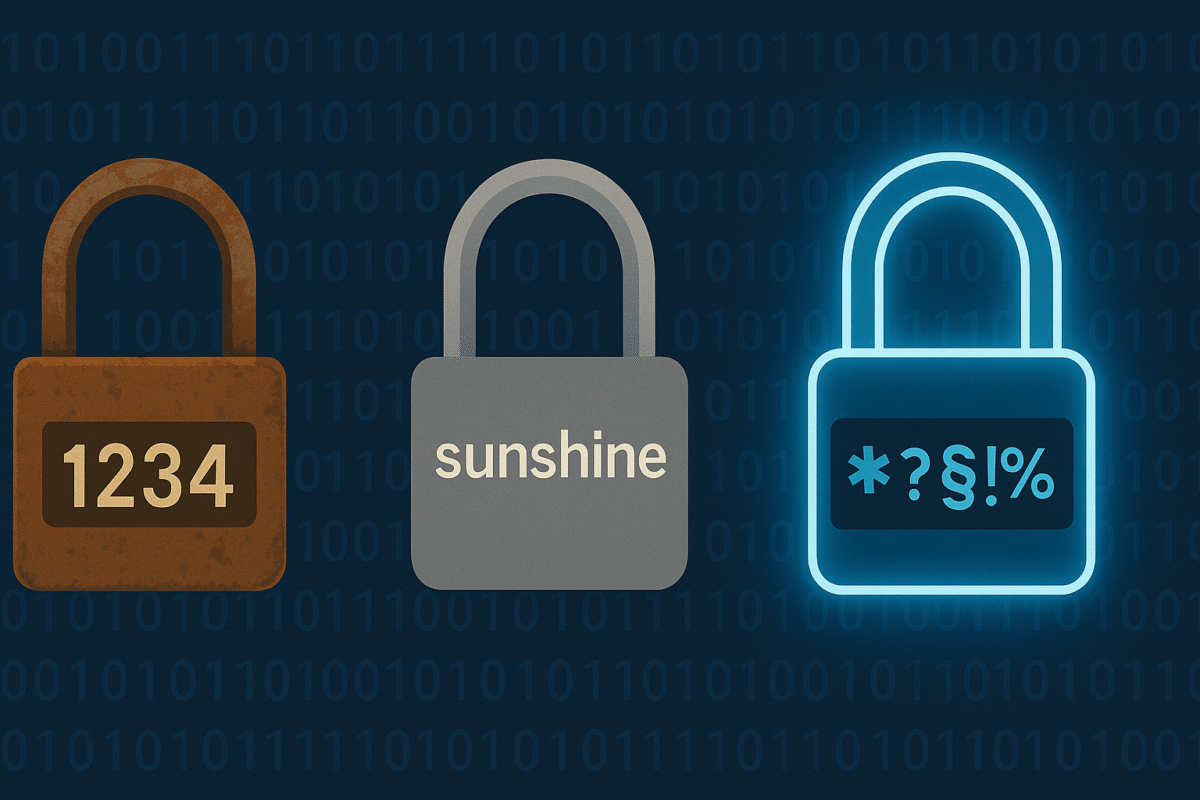
Why Passwords Matter (and Why Most People Get Them Wrong)
Passwords are the most common—and most frequently misunderstood—security mechanism on the planet.
Think about how many you have:
- Your main email
- Work account
- Social media
- Shopping sites
- Streaming services
- Wi-Fi
- Banking
- …and more!
But are all your passwords unique? Are any of them “password123” or “qwerty” or—gasp—your pet’s name?
If so, you’re not alone.
A good password is like a strong lock:
- Not easy to guess
- Not written on a sticky note
- Not shared with others
- Not reused everywhere
The Threats: How Attackers Break In
It’s time for a reality check. Attackers aren’t sitting at keyboards, guessing your password one by one.
They use automated tools—faster, smarter, and relentless.
The most common attacks:
- Dictionary Attack:
Attackers try every word in the dictionary. If your password is a common word (like “sunshine” or “dragon”), it’s toast. - Brute Force Attack:
This is the digital equivalent of trying every possible combination. Four digits? 10,000 possibilities. Four random letters? Over 7 million. Four random letters and numbers and symbols? 78 million. With enough time, even the strongest lock can be broken—unless it’s very complex. - Credential Stuffing:
If you use the same password everywhere and one site gets breached, attackers will try those same credentials on other sites.
(“Why not?” they think. “People are lazy!”)
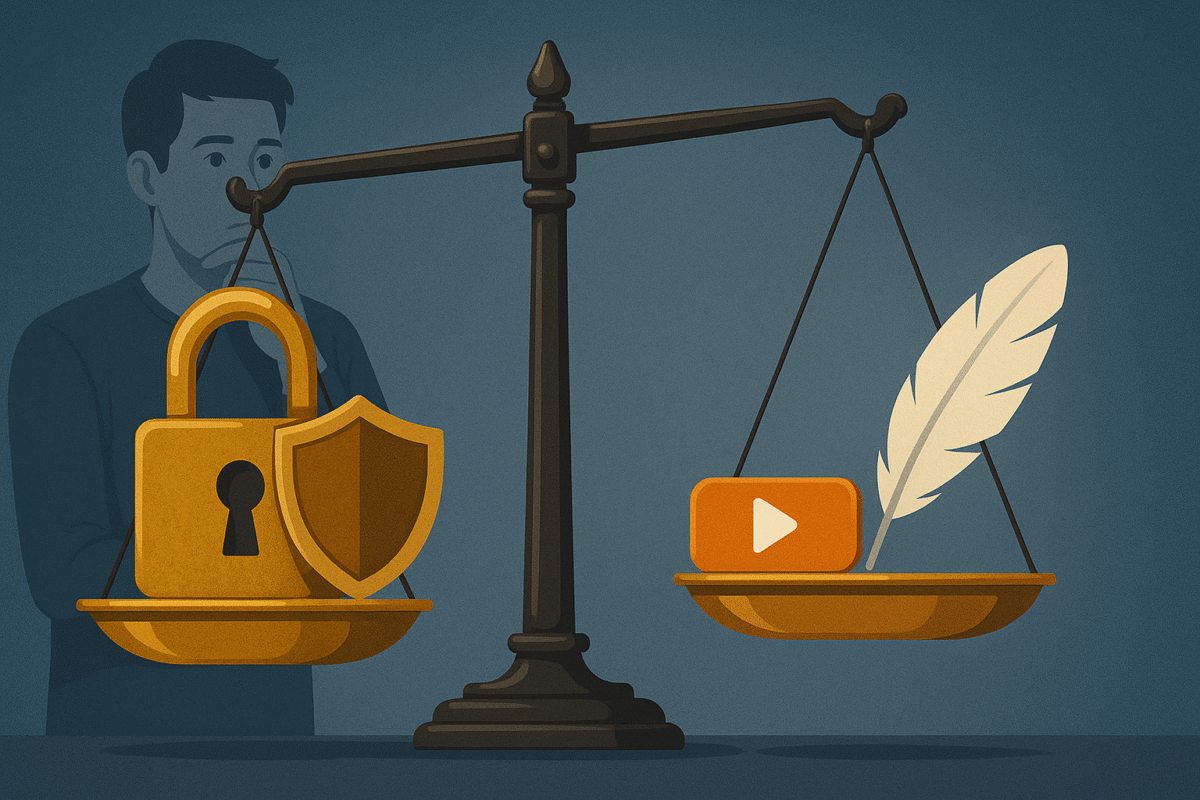
The Balancing Act: Security vs. Convenience
Let’s face it—long, complex passwords are a pain to remember.
But simple passwords are a hacker’s dream.
This is the eternal struggle in cybersecurity:
- More security means more complexity and hassle.
- More convenience means more risk.
Good security is about finding the sweet spot—and using tools and strategies that give you maximum protection with minimal friction.
Building Better Defenses: First Steps to Securing Your Accounts
You don’t have to become paranoid, but you should become aware.
Here are your first action steps (we’ll go deep into these in future posts):
- Use Unique Passwords for Every Account:
Don’t reuse! A breach on one site shouldn’t compromise everything you own. - Make Your Passwords Long and Complex:
8 characters is the bare minimum. 12–16 is better. Use a mix of letters, numbers, and symbols. - Enable Two-Factor Authentication (2FA):
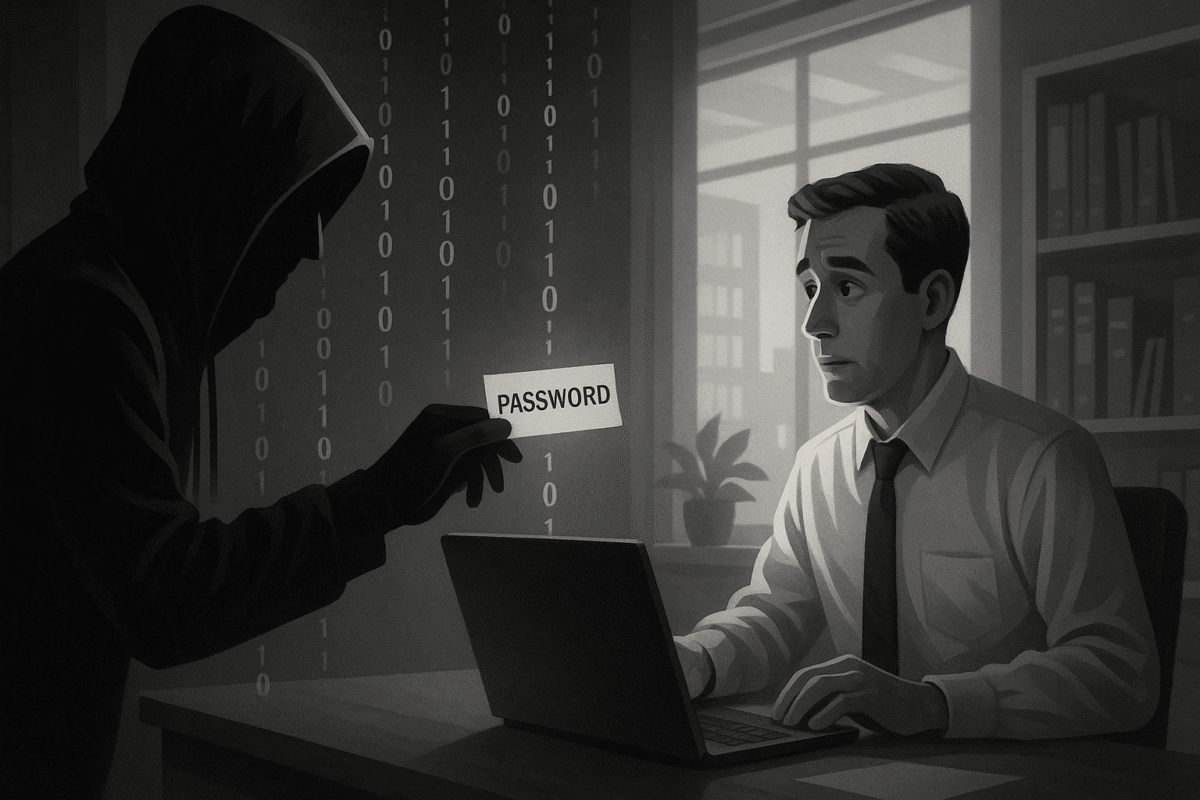
Whenever available, use 2FA—an extra layer of security that stops most attackers cold. - Watch for Phishing and Social Engineering:
Never give away your password. Be suspicious of emails or texts asking for login details, no matter how real they seem. - Use a Password Manager:
There are too many accounts for most people to remember strong, unique passwords for all. Password managers help you generate and store them securely (we’ll cover this in detail soon).
Why Should You Care? Real-World Stories
Still think you’re not a target?
Let’s get real.
- A college student gets locked out of their email because a weak password was guessed in seconds.
- A family loses access to their online photo albums after a phishing scam.
- A business loses thousands because an attacker used credential stuffing to access their payroll system.
It doesn’t just happen to “other people.”
Attackers use automated scripts that scan millions of accounts, looking for weak links. The next one could be yours—unless you make yourself a hard target.
Conclusion: Your Digital Journey Starts Here
Welcome to the start of your cybersecurity journey.
You don’t have to be a tech genius to stay safe—you just need the right habits, a little knowledge, and a willingness to take action.
In the posts that follow, we’ll break down each of these concepts step-by-step, showing you how to:
- Outsmart hackers and scammers
- Build ironclad defenses for your accounts
- Navigate the tricky balance between security and usability
Remember: cybersecurity isn’t about paranoia. It’s about empowerment.
So—are you ready to lock your digital doors?
Stay tuned for the next chapter, where we dive deeper into the world of passwords and how hackers try to crack them (and how you can stop them in their tracks).
People also search for:
Is cybersecurity a dead end job?
Why is cyber security not taken seriously?
Will cybersecurity jobs be replaced by AI?
Is cybersecurity really necessary?






