(How Today’s Security Stops Hackers in Their Tracks)
Introduction: Why the Old Password Alone Isn’t Enough
If you’ve been following our blog series, you already know that strong, unique passwords are essential—but in today’s world, even the best password can’t protect you from every threat. Cybercriminals have supercharged their tools: password-cracking software can try millions of guesses per minute, and phishing tricks are getting sneakier by the day.
So, how do modern websites and apps stay one step ahead?
They deploy layered defenses—like rate-limiting and multi-factor authentication (MFA)—to shut hackers down before they even get started.
Today, let’s break down these crucial technologies, why they matter, and how you can use them to keep your accounts safe.
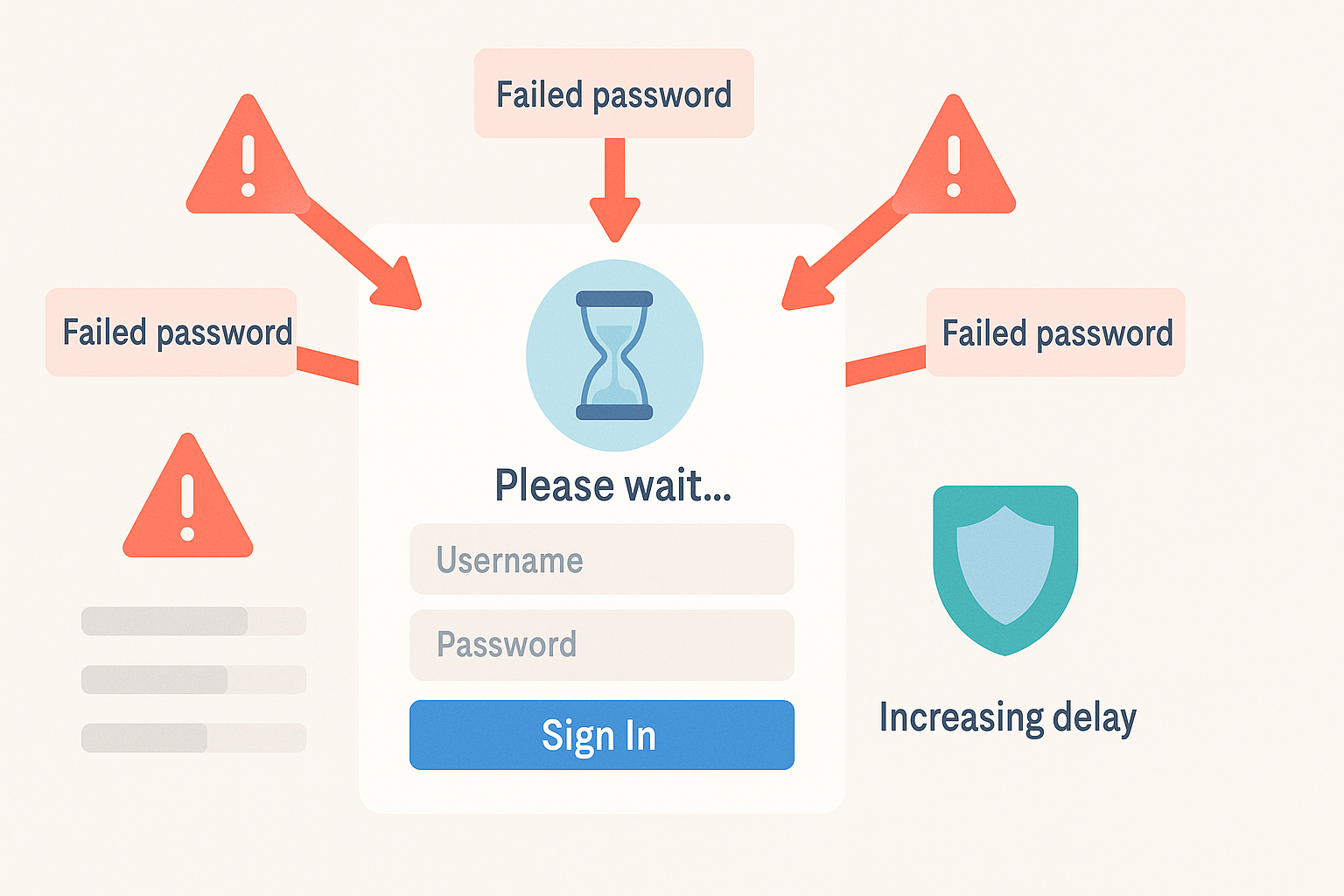
What is Rate-Limiting? (And Why Does It Matter?)
Imagine a bouncer at a club who lets people in one by one—and kicks out anyone who tries to rush the door. Rate-limiting does the same thing for your accounts:
It limits the number of login attempts you can make in a given time.
Why Rate-Limiting Stops Hackers
- Brute-force attacks rely on speed, sending thousands of password guesses per second.
- Without rate-limiting, hackers can try as many times as they like, making even strong passwords vulnerable over time.
- With rate-limiting, every failed login attempt triggers a pause—sometimes for seconds, minutes, or even hours.
Example:
Apple’s iPhones lock users out for increasing time intervals after repeated failed passcode attempts. Most banks, email providers, and social networks do the same.
Result:
Even if a hacker knows your username, they can’t just “brute-force” their way in.
How Rate-Limiting Works (A Step-By-Step Walkthrough)
- A user enters the wrong password.
The website tracks this failed attempt. - The user tries again (and fails).
After a set number of wrong tries (maybe 3–5), the system introduces a delay. - If attempts keep failing:
The delays get longer—or the account is temporarily locked and can only be reset via email or SMS.
Rate-Limiting Variations
- Time-based lockout: Wait 30 seconds, then try again.
- Account lockout: After 5 failed attempts, account is locked for 30 minutes.
- CAPTCHA requirement: Proves you’re human, not a bot.
- Progressive delays: Each failure adds more waiting time.
Why Not All Sites Use Rate-Limiting
- Some websites are still catching up.
- Others fear locking out legitimate users (which is why password managers are so helpful—fewer typos!).
Pro tip:
If a site doesn’t have rate-limiting, be extra careful—use a stronger, unique password and enable all extra protections.
Enter Multi-Factor Authentication (MFA): The Gold Standard
If passwords are the lock, multi-factor authentication is the deadbolt and security camera all in one.
MFA (sometimes called two-factor authentication, or 2FA) requires something in addition to your password.
The Three Factors of Authentication
- Something you know: Your password or PIN.
- Something you have: Your phone, a hardware token, or an authenticator app.
- Something you are: Biometrics (fingerprint, face scan, retina).
Most systems use a combination of two.
For example, after entering your password (something you know), you’ll get a code on your phone (something you have).
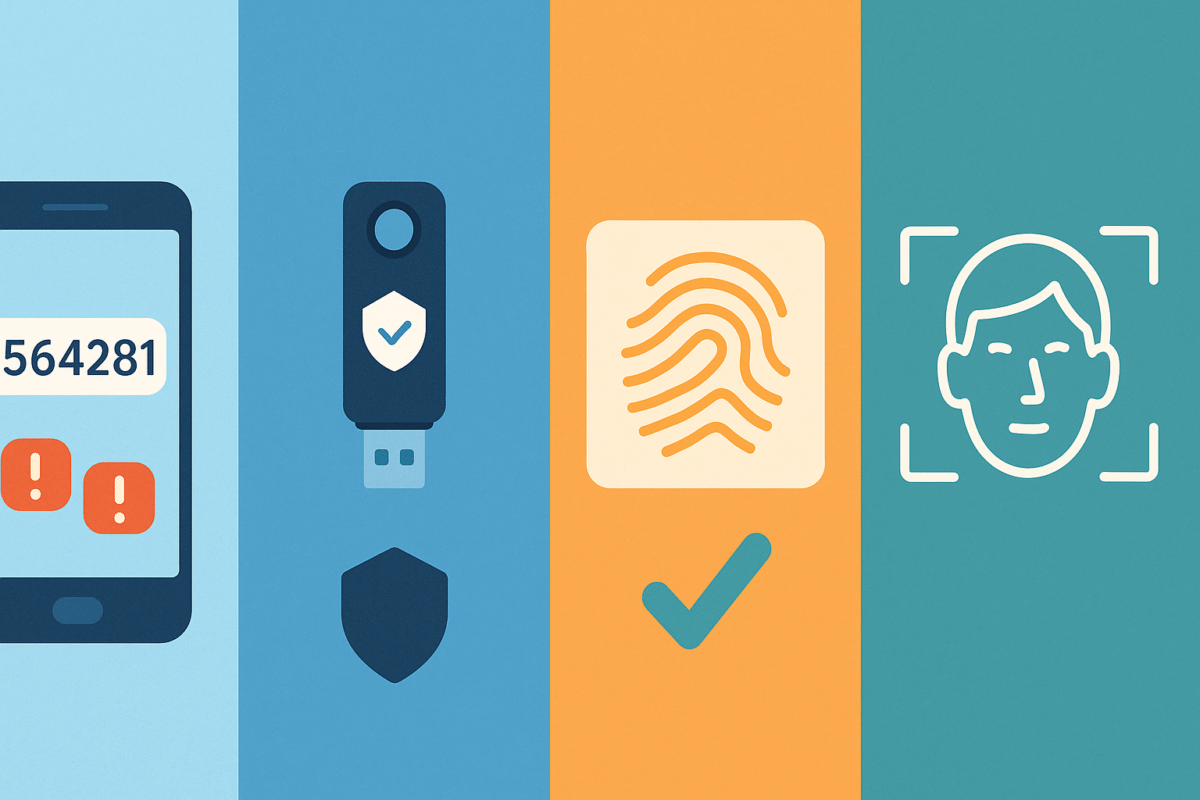
Types of MFA: What’s Out There?

- SMS-based Codes:
A one-time code sent via text message.
Downside: Can be intercepted by SIM swapping or social engineering. - Authenticator Apps:
Time-based one-time passwords (TOTP) from apps like Google Authenticator, Microsoft Authenticator, or Authy.
Stronger than SMS—codes refresh every 30 seconds and aren’t tied to your phone number. - Hardware Security Keys:
Physical devices (like YubiKey or Titan Security Key) that plug into your computer or phone.
Practically unhackable unless stolen. - Biometrics:
Fingerprint, face recognition, or retina scan—fast and unique to you.
Pro tip:
Use app-based or hardware MFA wherever possible—SMS is better than nothing, but not as strong.
How MFA Shuts Down Hackers
Even if a hacker steals your password, they can’t access your account without the second factor.
- Phished your credentials? They’d also need your phone or hardware key.
- Guessed your password? They’re still locked out by that one-time code or biometric check.
Stat:
Microsoft reports that MFA blocks over 99% of automated attacks. It’s that powerful.
How to Enable MFA On Your Accounts (A Step-By-Step Guide)
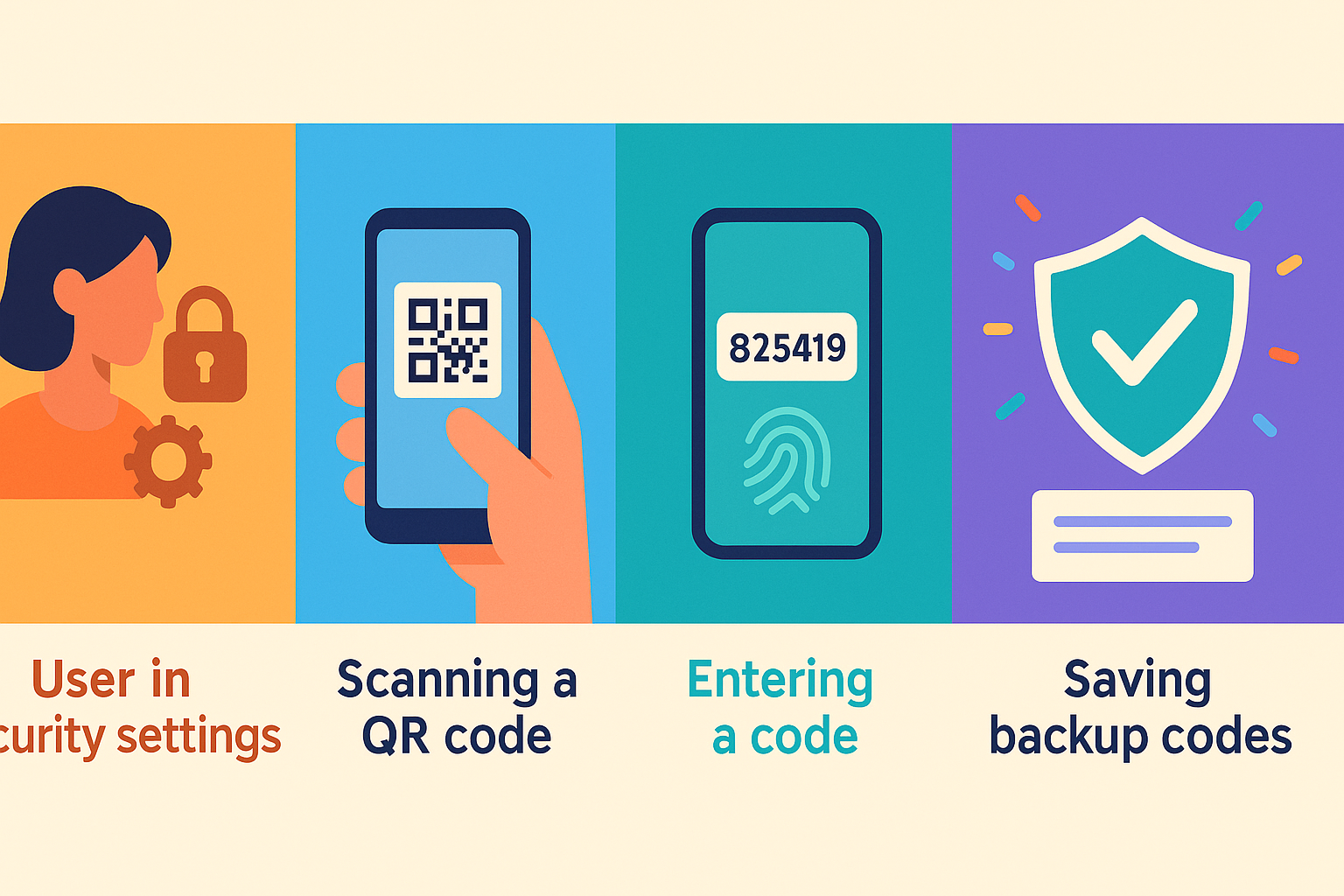
- Go to your account’s security settings.
- Look for “Two-Factor” or “Multi-Factor Authentication.”
- Choose your preferred method: SMS, app, hardware key, or biometric.
- Follow the setup instructions.
Most sites display a QR code to scan with your authenticator app. - Save backup codes somewhere safe!
In case you lose your device, you’ll need these to recover access.
Popular sites supporting MFA:
- Google, Microsoft, Apple
- Facebook, Twitter/X, Instagram
- Banks and credit cards
- Dropbox, Amazon, GitHub, and many more
The Human Element: Rate-Limiting and MFA in Daily Life
- Forgot your password?
Rate-limiting and MFA make recovery safer—only you, with your second factor, can reset access. - Traveling or switching phones?
Plan ahead—update MFA methods, and keep backup codes handy. - Lost your phone?
Use recovery codes or hardware tokens to regain access.
Remember:
These defenses don’t just protect you—they protect everyone in your digital network.
Modern Security Checklist: What You Can Do Right Now
- Audit your critical accounts:
Turn on MFA everywhere possible. - Check for rate-limiting:
Test login attempts and see how your sites respond. - Update weak passwords and use a password manager.
- Educate friends and family:
Show them how MFA and rate-limiting work. - Stay alert for phishing attempts, even with MFA enabled.
Conclusion: Stack Your Defenses—And Sleep Easier
In the arms race between hackers and the rest of us, the old “just use a good password” advice is no longer enough.
Layered defenses—like rate-limiting and multi-factor authentication—turn your accounts into digital fortresses. With just a few clicks, you can lock down your data, block brute-force attacks, and rest easy knowing you’ve outsmarted even the cleverest cybercriminals.
Don’t wait:
Enable MFA, make sure your accounts rate-limit login attempts, and encourage your friends, family, and colleagues to do the same.
Up next: We’ll break down the strengths and weaknesses of the most common MFA methods—and how to choose what’s right for you.





