(The Invisible Threats Lurking Behind Your Keyboard—and How to Beat Them)
Introduction: The Hidden Dangers on Every Device
You change your passwords regularly, use two-factor authentication, and have a password manager.
So you’re safe, right?
Not so fast. In the world of cybersecurity, not all threats knock politely at your digital door. Some slither in quietly, hiding in plain sight and striking when you least expect it.
Welcome to the world of malware, keyloggers, and device security—where the biggest risks are often invisible. Today, we’ll shine a light on these digital pests, show you how they work, and give you the tools to lock down every device you own.
What Is Malware? (And Why Should You Care?)
Malware (malicious software) is a catch-all term for any software designed to harm, exploit, or otherwise compromise your device or data.
It’s the Swiss Army knife of cybercrime:
- Viruses: Spread from file to file, often via downloads or email attachments.
- Trojans: Masquerade as legitimate software but perform hidden, harmful actions.
- Ransomware: Encrypts your data and demands payment for release.
- Spyware: Silently monitors your activity, collecting data for attackers.
- Keyloggers: Record everything you type—including your passwords.
Malware is everywhere: in phishing emails, shady downloads, infected USB drives, even malicious ads.
Keylogging: How Hackers Steal Your Secrets Keystroke by Keystroke
Keyloggers are among the most dangerous forms of malware. They run silently in the background, recording every keystroke you make—usernames, passwords, credit card numbers, private messages—and send them back to hackers.
Keyloggers can be:
- Software-based (installed via malware, hidden in apps or browser extensions)
- Hardware-based (small devices plugged into your keyboard or computer)
How Do You Get Infected?
- Downloading pirated or cracked software
- Opening malicious email attachments or links
- Plugging in unknown USB devices
- Using public or shared computers
Real-World Consequences: Stories from the Front Lines
- A small business owner lost thousands after a keylogger sent her online banking password to a remote hacker.
- A student had their email and social accounts compromised after installing a free game from an untrusted website.
- A hospital suffered a ransomware attack, locking doctors out of patient records for days—all starting with a single malicious email.
Lesson: You can have the world’s strongest passwords and 2FA—but if a keylogger is watching, nothing is safe.
How Malware Gets Past Your Defenses
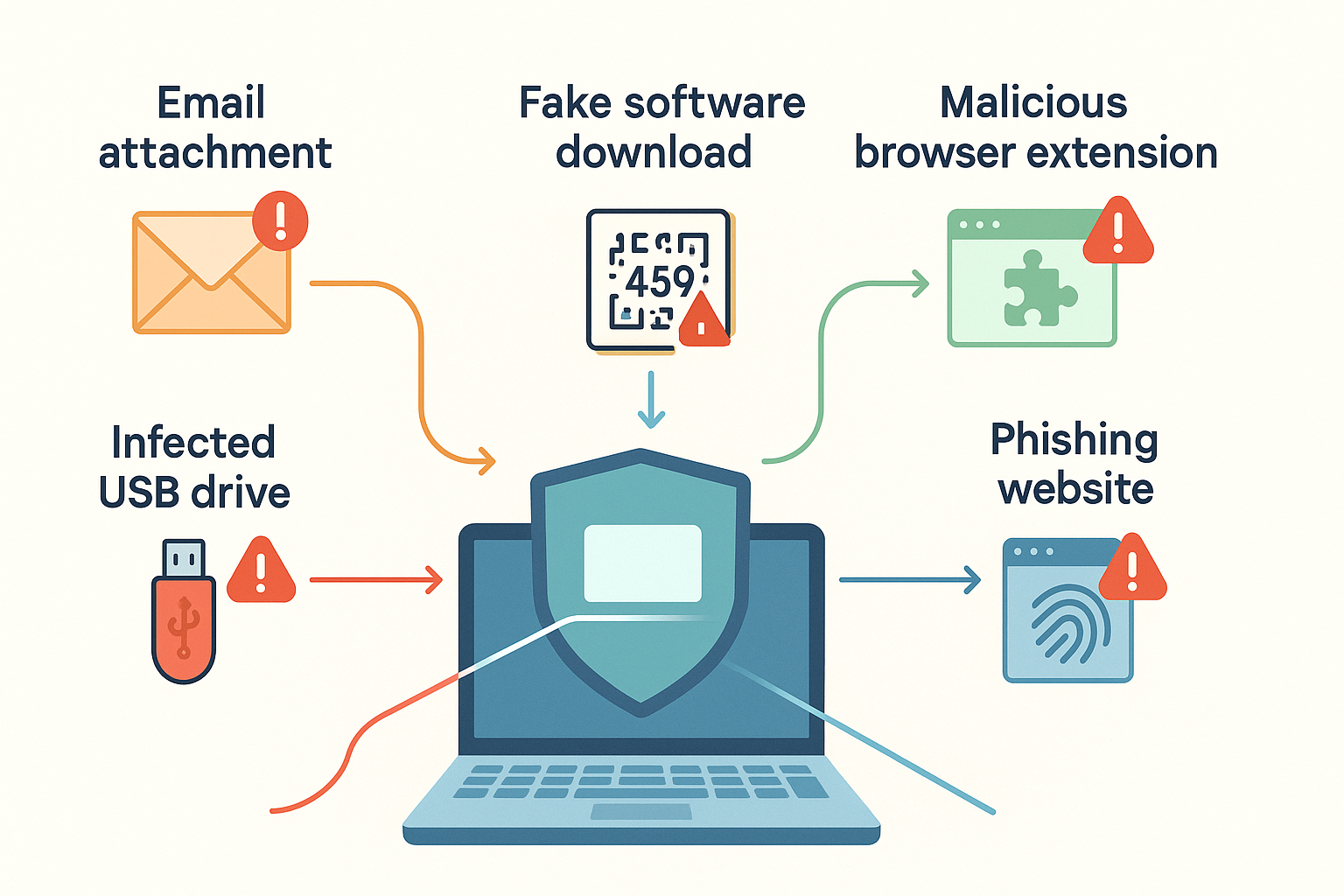
Cybercriminals are masters of disguise:
- They mimic legitimate apps or updates
- Hide malicious code in fake invoices or “urgent” attachments
- Use social engineering to trick you into disabling antivirus or installing “fixes”
And once malware is on your device, it can:
- Record your keystrokes (keylogger)
- Take screenshots or record audio/video
- Steal files, cookies, or saved credentials
- Spread to other devices on your network
Protecting Yourself: The Device Security Essentials

1. Keep Everything Updated
- Software updates patch security holes that malware can exploit.
- Always update your operating system, browser, and all apps—especially security software.
2. Use Strong Antivirus and Anti-Malware Tools
- Install reputable antivirus/anti-malware programs and keep them up to date.
- Enable real-time protection and schedule regular scans.
3. Download Only from Trusted Sources
- Avoid pirated/cracked software and unknown sites.
- Stick to official app stores and reputable websites.
4. Beware of Phishing and Suspicious Attachments
- Never open email attachments or click links from unknown senders.
- Check URLs carefully—phishing sites often look nearly identical to the real thing.
5. Physically Secure Your Devices
- Don’t leave laptops or phones unattended in public.
- Beware of hardware keyloggers—check your ports and never use unfamiliar USB drives.
6. Use Unique, Strong Passwords and MFA
- Even if malware compromises one account, it won’t open every door.
- MFA can stop some attacks—even if a password is stolen.
Device Hygiene: Good Habits for Safe Computing
- Restart your devices regularly.
Some malware is memory-resident and vanishes after a reboot. - Log out of important accounts when using shared or public computers.
- Avoid browser extensions unless absolutely necessary—many are a privacy nightmare.
- Encrypt your device.
Most modern phones and computers offer full-disk encryption. If your device is stolen, your data stays locked. - Back up your data.
Ransomware can destroy everything. Keep backups—offline or in secure cloud storage.
What To Do If You Think You’re Infected
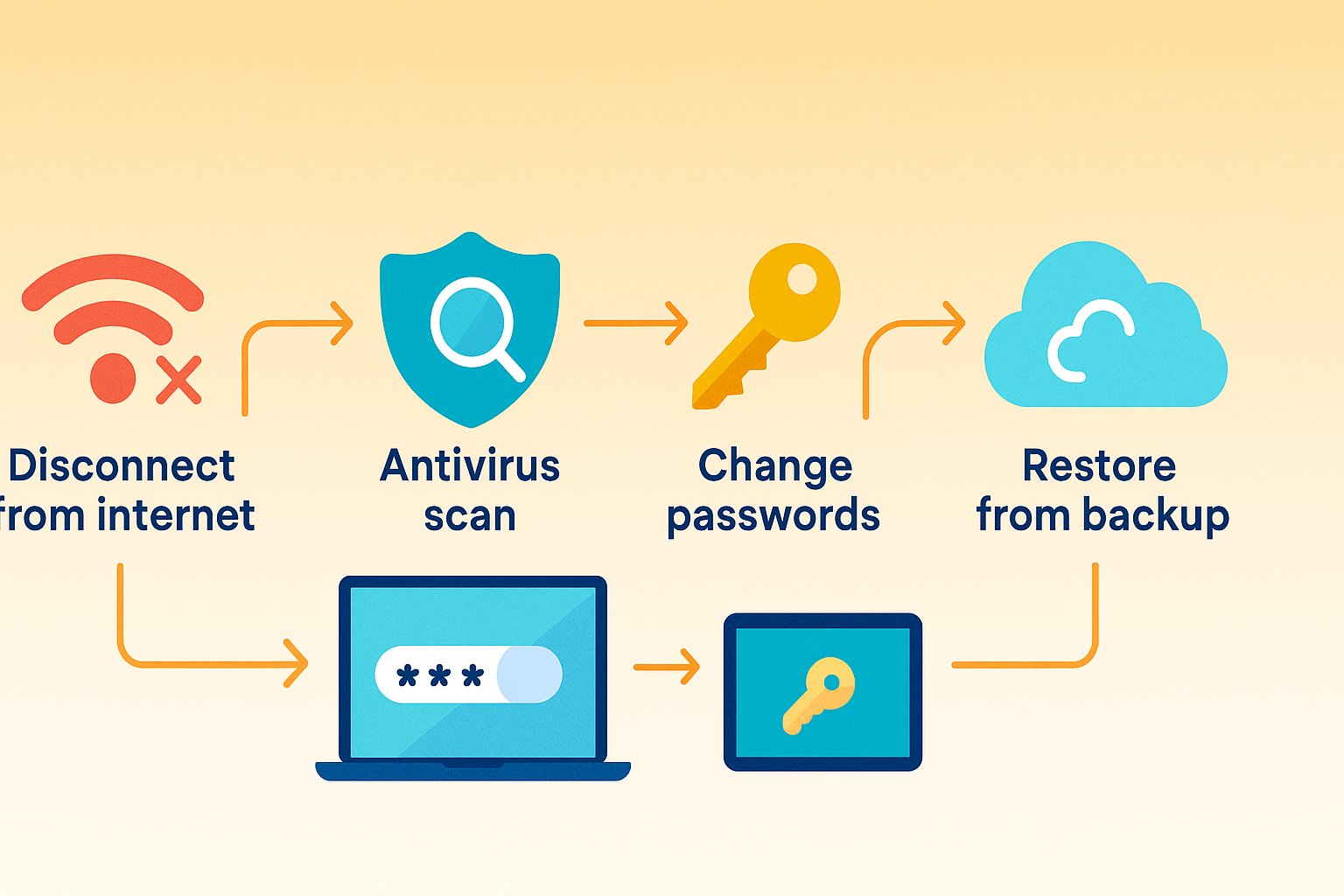
- Disconnect from the Internet to prevent data from being sent to attackers.
- Run a full antivirus/anti-malware scan and quarantine/remove any threats.
- Change your passwords (from a clean device).
- Enable 2FA everywhere you can.
- Restore from a backup if necessary—sometimes a full reset is safest.
- Consider professional help if you’re unsure.
Advanced Defenses: For Power Users
- Use a dedicated security key (YubiKey, Titan) for critical accounts.
- Set up separate user profiles for work, browsing, and banking.
- Employ “sandboxed” environments or virtual machines for risky downloads.
- Regularly audit device permissions and running processes.
Conclusion: The Battle Is Invisible—But You Can Win
You can’t see keyloggers, malware, or spyware—but they can see everything you do. With good device hygiene, strong security tools, and the right habits, you can stay one step ahead of cybercriminals and keep your data, your privacy, and your peace of mind safe.
Remember:
- Keep everything updated
- Use trusted security software
- Watch for phishing
- Lock down your devices
Security is a journey, not a destination. Start today—because the threats are already here.




