(How Modern Hackers Trick You—And How To Outsmart Them Every Time)
Introduction: The Human Side of Hacking
You can have the world’s strongest password, the best antivirus software, and two-factor authentication, but if you don’t know the tricks hackers use to manipulate people, you’re still a target.
The weakest link in any security system is always the human.
This is why hackers have become experts at targeting people through methods like credential stuffing, social engineering, and phishing.
Let’s lift the curtain on how these attacks work in the real world—and, more importantly, how you can spot them before it’s too late.
Part 1: Credential Stuffing—How Password Reuse Puts You at Risk
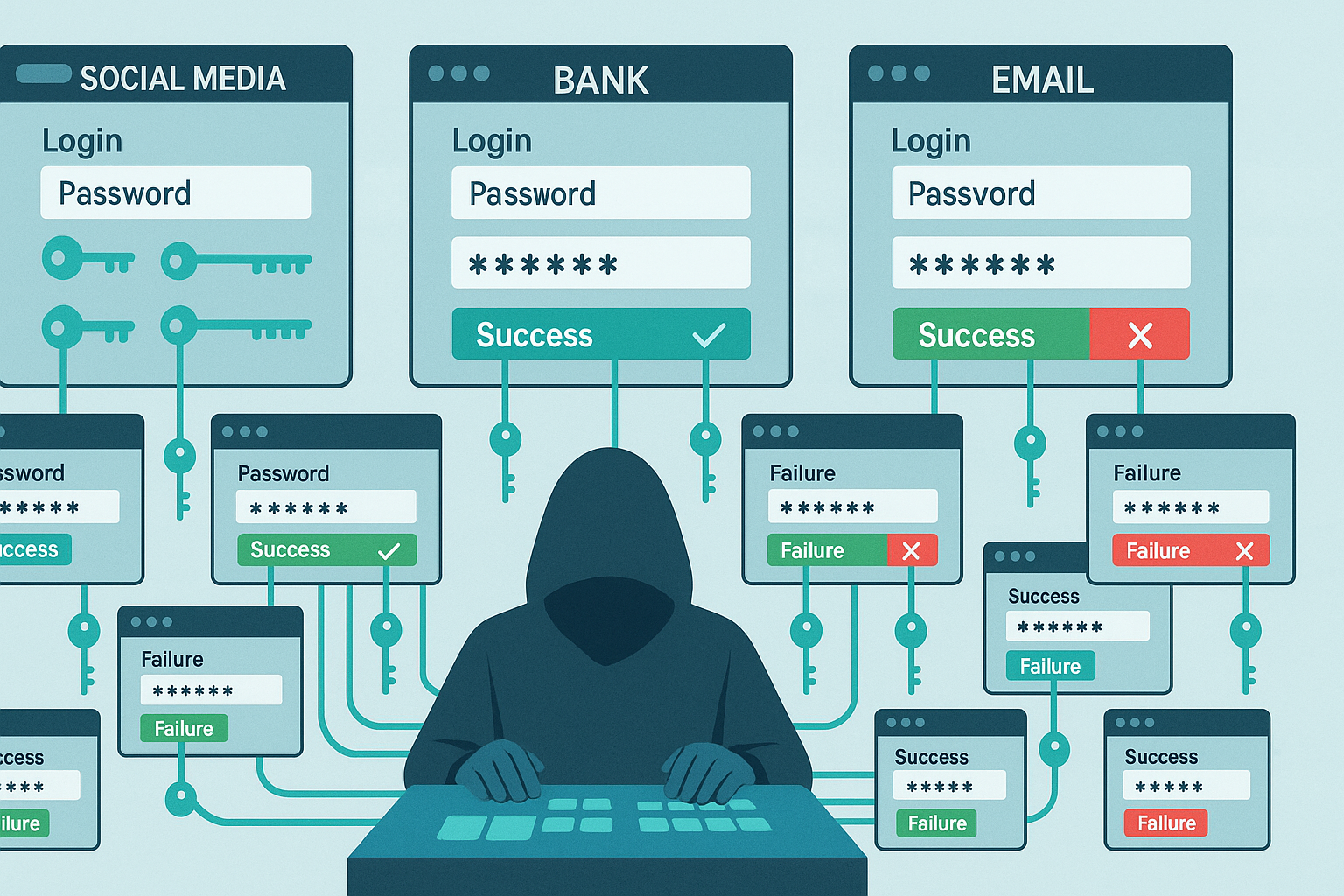
What Is Credential Stuffing?
Imagine you lose your apartment keys—and someone finds out you use the same key for your house, car, and office.
Credential stuffing is a cyberattack that works on the same idea:
Hackers use stolen username and password pairs from one site to try to log into as many other sites as possible.
How It Works
- Data breaches at big companies (or small forums) spill millions of credentials onto the dark web.
- Hackers use automated tools to rapidly test these stolen credentials on other websites—banking, email, social media, you name it.
- If you reused a password anywhere, attackers are in.
Real-World Example
- In 2019, the “Collection #1” breach dumped 773 million email/password pairs online.
- Within days, people saw unauthorized logins to social media, gaming accounts, even work email.
How To Protect Yourself
- Use a unique password for every account.
- Enable two-factor authentication.
- Check your email on HaveIBeenPwned.com to see if you’ve been in a breach.
- Change passwords immediately if reused on other sites.
Part 2: Social Engineering—Hacking the Human, Not the System
What Is Social Engineering?
Forget Hollywood’s image of hackers furiously typing code in a dark room.
The most effective hackers simply talk their way in.
Social engineering is the art of manipulating people into revealing confidential information or performing actions that compromise security.
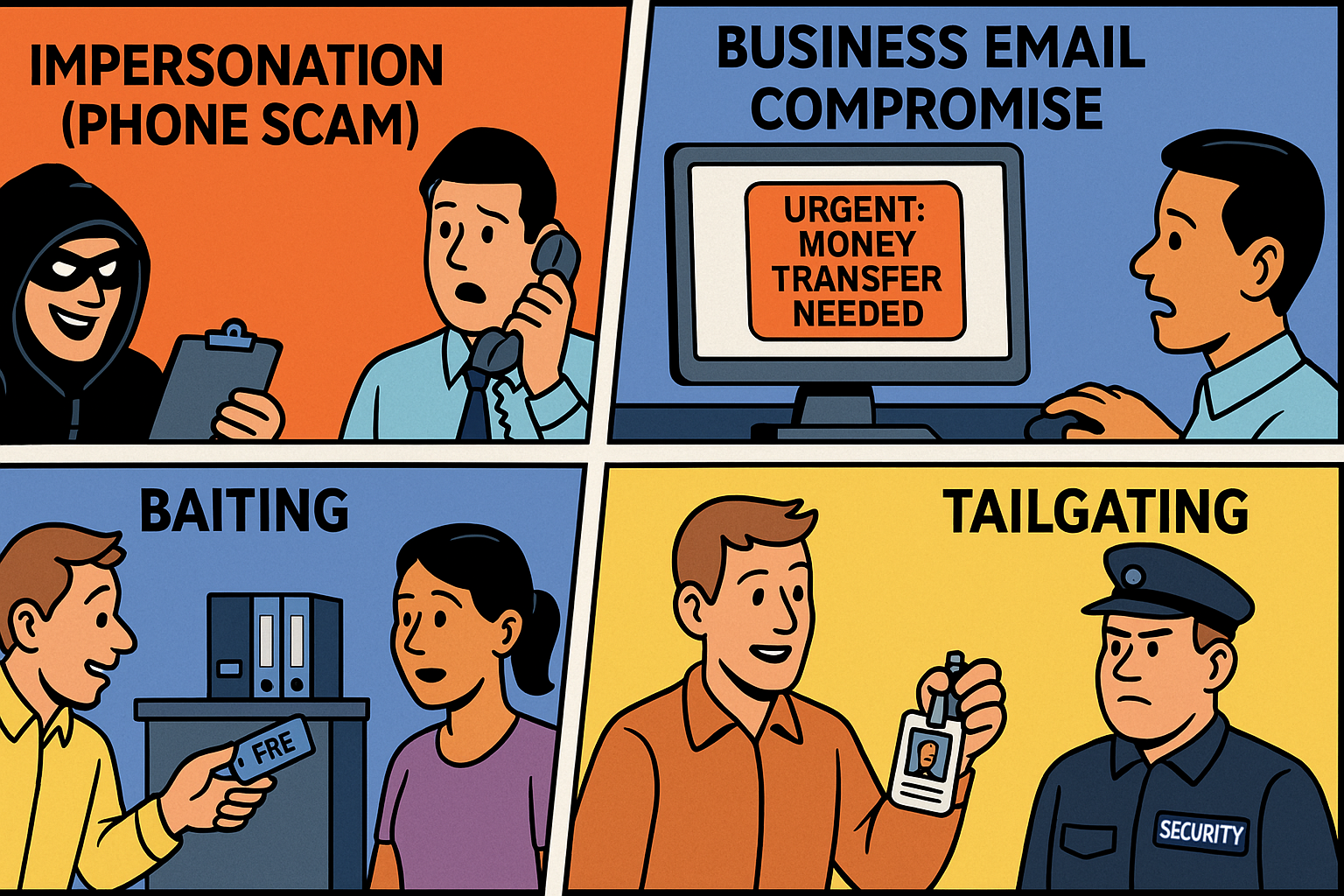
Common Social Engineering Techniques
- Impersonation
Pretending to be someone trusted (tech support, your boss, bank staff). - Pretexting
Creating a believable story or scenario to trick someone into giving up info. - Urgency and Fear
“Your account will be deleted unless you verify NOW!”
Scaring users into fast, careless actions. - Baiting
Offering something tempting (like free software or USB sticks) laced with malware.
Real-World Social Engineering Scams
- CEO Fraud:
An attacker pretends to be a company executive and emails staff to urgently transfer money or send sensitive info. - Tech Support Scams:
Fake Microsoft/Apple “support” calls ask for remote access or payment.
How To Protect Yourself
- Slow down!
Hackers want you to act fast and skip logic. - Verify identities through official channels.
- Never share sensitive info (passwords, codes) via email, phone, or text.
- Educate yourself and others—awareness is your strongest shield.
Part 3: Phishing—The Bait That Catches Millions
What Is Phishing?
Phishing is the act of sending fake emails, texts, or messages that look legitimate to trick you into revealing personal data—especially passwords or financial info.
Types of Phishing Attacks
- Email Phishing:
Fake messages pretending to be from banks, popular sites, or colleagues with links to fake login pages. - Spear Phishing:
Targeted attacks using details about you (name, job, contacts) to make the message even more convincing. - Smishing and Vishing:
SMS (smishing) or voice calls (vishing) that pretend to be from real organizations. - Clone Phishing:
Replicating a legitimate email but replacing a link or attachment with something malicious.
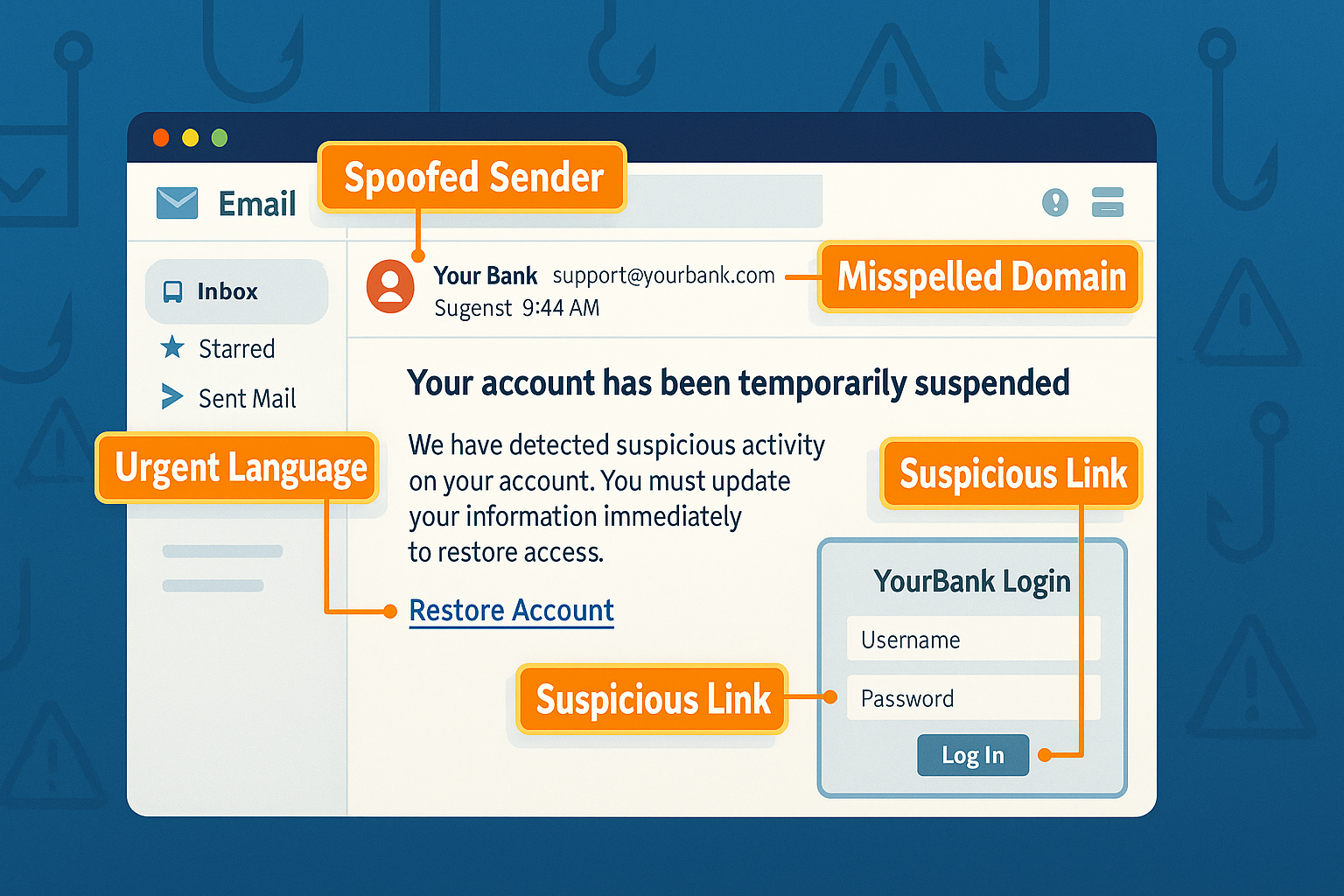
Signs of a Phishing Attempt
- Unusual sender address or misspelled domain names
- Unexpected links or attachments
- Generic greetings (“Dear Customer”)
- Urgency or threats
- Requests for sensitive info
- Poor grammar or formatting
How to Protect Yourself from Phishing
- Hover over links before clicking—check the actual URL.
- Don’t download attachments from unknown sources.
- When in doubt, contact the sender directly using official contact methods.
- Use email security filters and up-to-date antivirus.
- Report suspicious emails to your IT or email provider.
Part 4: Outsmarting Modern Attackers—Your Step-By-Step Defense

- Never reuse passwords—credential stuffing relies on this.
- Educate yourself and your family/team—awareness blocks most social engineering.
- Stay skeptical of urgent requests—verify by phone or in person.
- Use password managers—they won’t auto-fill on fake sites.
- Enable two-factor authentication—even if a password leaks, it’s not enough.
- Keep your devices and software updated—patches fix security holes.
Conclusion: Trust, But Verify—And Stay Ahead
Hackers don’t need to outsmart your computer—they only need to outsmart you.
The good news? With vigilance, strong habits, and a little healthy skepticism, you can beat them at their own game.
Remember:
- Don’t reuse passwords
- Stay skeptical
- Verify, verify, verify
Share this post to help others get smart about modern cyber threats.
Next up: How to use password managers and single sign-on (SSO) to simplify your security and strengthen your digital fortress.





