(How Passwords Really Work—And Why They’re Your First Line of Defense)
Introduction: Behind Every Login—A Story of Trust
Have you ever paused, just for a moment, as you typed in your password?
Maybe your fingers flew across the keyboard with muscle memory, or maybe you fumbled, clicking “Forgot Password?” for the umpteenth time. But every login—every password prompt—isn’t just a barrier. It’s the digital world’s way of asking: “Can you prove who you say you are?”
Let’s peel back the screen and see what’s really happening every time you log in. Welcome to the world of passwords and authentication—the unsung guardians of your online life.
What Are Passwords, Really? (And Why Are They So Annoying?)
If you’ve ever rolled your eyes at a “Create a strong password” prompt, you’re not alone. Passwords are a love-hate relationship for everyone.
But at their core, passwords are ancient—descendants of secret handshakes, coded messages, and locked doors. They’re your first—and sometimes only—defense against a world full of digital pickpockets.
The Role of Passwords
A password is a “shared secret” between you and a system. It’s the answer to the world’s oldest question:
“Are you really you?”
- If yes, come on in!
- If not, stay out.
A username is often public. Your email address, for example, can be found by friends, marketers, or (unfortunately) attackers.
Your password, though, is private—known only to you (and, hopefully, no one else).
Why Do We Need Passwords at All?
Think about all the digital “rooms” you enter every day:
- Email
- Social media
- Online banking
- Shopping
- Work systems
- Streaming services
Each “room” needs a key—and if your key is too simple, someone else can easily make a copy.
Authentication: Proving You Are Who You Say You Are
Authentication is the formal word for the “ID check” that happens when you log in.
It’s more than just typing a password. It’s a negotiation—a system’s way of saying, “I know lots of people might know this username, but only one should know this password.”
How Authentication Works
- You present your credentials (username and password).
- The system checks: Does this password match what’s stored for this user?
- Access granted—or denied.
It’s simple, but this dance of secrets forms the backbone of almost every digital interaction you have.
Authorization: What Can You Access Once You’re In?
It’s one thing to prove your identity.
It’s another thing to prove you deserve access.
- Authentication: Proves your identity.
- Authorization: Decides what you can do.
Think of authentication as showing your office badge at the building’s front door. Authorization is whether your badge opens the executive suite, the server room, or just the lobby.
You want systems that not only recognize you—but also set appropriate boundaries.
How Passwords Are Attacked (And How to Outsmart the Bad Guys)
Passwords are everywhere—and attackers know it.
They don’t guess passwords by hand; they use clever tricks and powerful computers. Let’s explore the biggest threats, so you can spot them coming:
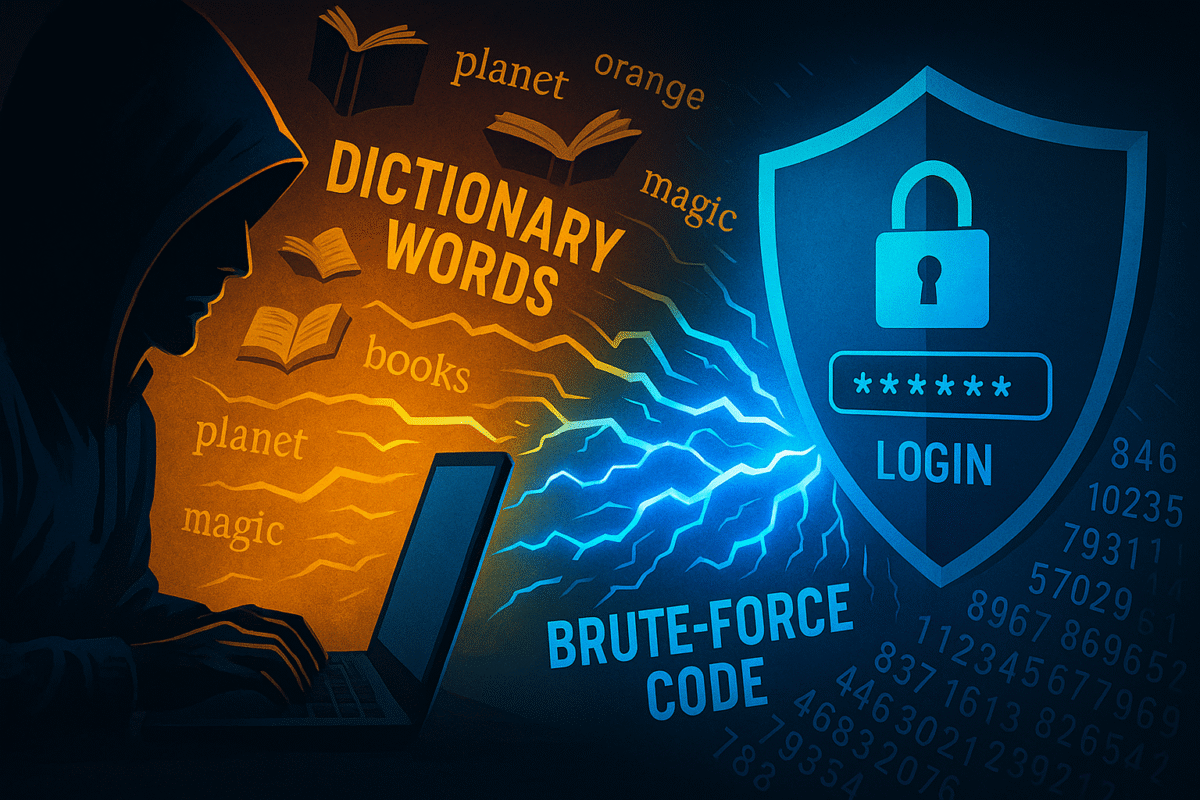
1. Dictionary Attacks
Attackers try every word in the dictionary—literally!
If your password is “sunshine” or “football” or “monkey,” you’re an easy target.
Lesson:
Never use actual words or predictable phrases.
2. Brute Force Attacks
This is “try everything, eventually something works.” Computers race through every combination—especially if your password is short or simple.
- A 4-digit PIN? Only 10,000 possible combos—trivial for a computer.
- A short password with only letters? Still easy to crack.
Lesson:
The longer and more random your password, the safer you are.
3. Credential Stuffing
Ever reused the same password on multiple sites? If one gets breached, attackers will try those credentials everywhere.
- Same password for email and Facebook? If either site is hacked, you’re exposed on both.
Lesson:
Never reuse passwords—every account deserves its own key.
The Math Behind Password Security: Why Size (and Complexity) Matters
Let’s get nerdy for a second—because it’s actually empowering.
- A 4-digit numeric PIN (0–9) has 10,000 possible combos.
- A 4-letter password (a–z, A–Z) has over 7 million possibilities.
- Add numbers and symbols? Now you’re talking tens of millions—even billions—for longer passwords.
But computers are fast. What’s hard for humans isn’t always hard for code.
Bottom line:
- Short = bad.
- Simple = bad.
- Long, random, and complex = good.
Why Sites Demand Complex Passwords (and Why You Should Care)
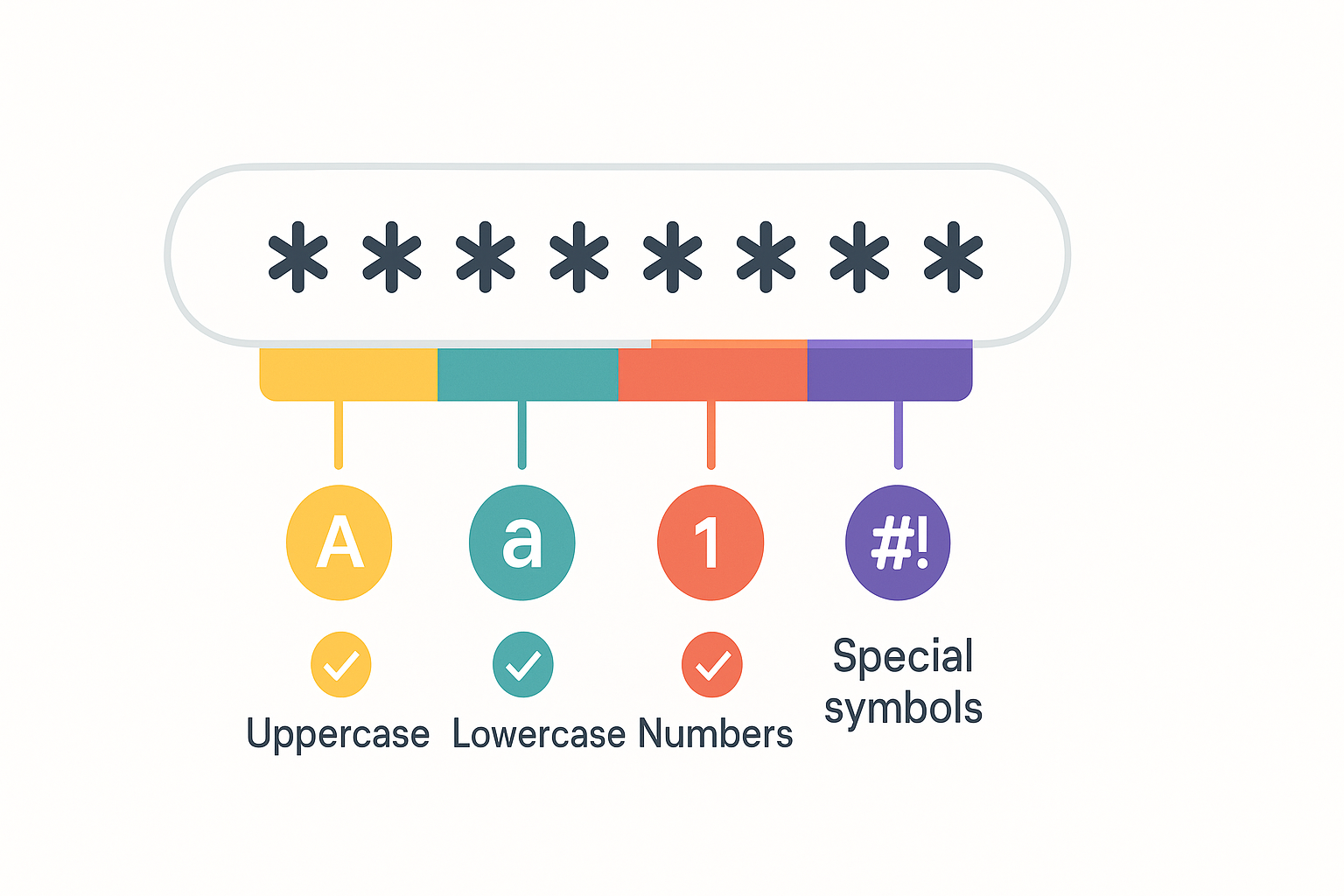
You might groan at password requirements (“Must contain an uppercase, lowercase, number, symbol, AND be at least 8 characters!”), but there’s logic behind it.
- Too short: Easy for attackers to guess.
- Just words: Vulnerable to dictionary attacks.
- Patterns like ‘123456’ or ‘password’: Instantly guessed.
A good password is:
- At least 8–12 characters (the longer, the better).
- Mixes upper/lowercase, numbers, and symbols.
- Not based on public info (like your birthday or favorite team).
Pro tip:
Consider using a passphrase—a string of random words or a sentence you’ll remember but others can’t guess.
Password Management: How Real People Can Actually Survive

You might be thinking, “But I have dozens (maybe hundreds!) of accounts. How can I possibly remember all these unique, complex passwords?”
That’s where tools and strategies come in:
1. Password Managers
Password managers generate, store, and auto-fill complex passwords for every site. You only need to remember one strong master password.
- Examples: LastPass, 1Password, Bitwarden, browser-integrated managers.
2. Single Sign-On (SSO)
Some sites let you log in with Google, Facebook, or Apple. This reduces the number of passwords you need to remember, but comes with its own risks (if that one main account is compromised, everything else is vulnerable).
3. The Password Reset Trick
Don’t rely on it! Attackers can use password reset links if your email isn’t secure. Always protect your email account with the highest level of security.
The Rise of Two-Factor Authentication (2FA): An Extra Lock on Your Digital Door

Password alone isn’t enough anymore. Many sites offer (or require) a second layer of protection.
- Something you know: Your password.
- Something you have: Your phone (SMS code, authenticator app), a hardware token.
- Something you are: Biometrics (fingerprint, face recognition).
2FA makes it exponentially harder for attackers. Even if they get your password, they still need your phone or fingerprint.
Common Pitfalls and How to Avoid Them
1. Password Hints and Security Questions
Attackers can often find your “first pet’s name” or “mother’s maiden name” from social media.
Solution: Use random answers that only you know.
2. Writing Passwords Down
Sticky notes on your monitor? An Excel file named “passwords”?
Don’t do it. If you must write them, keep the list in a locked, safe place—and never label it obviously.
3. Falling for Phishing
Never enter your password on a site you reached from a suspicious email or link.
When in doubt, open a new tab and type the site’s address yourself.
The Human Factor: Usability vs. Security
There’s always a trade-off:
- Make passwords too complex, and users forget (or write them down unsafely).
- Make passwords too simple, and attackers get in.
Good security balances convenience and strength.
Start with your most important accounts (email, banking, work), then expand. Use password managers, enable 2FA, and stay alert.
Conclusion: You Are the First and Last Line of Defense
Passwords aren’t perfect—but they’re your first line of digital defense.
Master the basics, avoid the common mistakes, and you’re already ahead of most people online.
In the next post, we’ll dive deeper: How hackers REALLY crack passwords (and how you can build defenses that actually work).
Ready to level up your digital security? Bookmark this series, share it with friends and family, and take control of your digital life.
Still have password questions? Drop them in the comments! And if you haven’t already, start using a password manager today—it’s your secret weapon against cybercrime.
People also search for:
What are the basics of authentication?
What is password and authentication?
What is PAP in cybersecurity?
What is the 3 level password authentication system?





